David Huerta is a technologist who recently published a provocative work to make everyone think a little bit more about privacy and what governments should be allowed to do or not:
I work outside the Pokemon business model of catching every user’s data or abusing it for state surveillance. I work instead surrounded by priceless art and in giving it a voice inside and outside the thick, Faraday cage walls of the museum it lives in.
He created an encrypted mixtape and sent it to NSA. The device runs on Arduino and other open hardware and for David is a:
machinery that can be trusted not to spy on you because of the disclosure of its design, schematics and bill of materials to anyone who wishes to inspect, build, or build upon the device. The device contains a soundtrack for the modern surveillance state. It’s designed to be enjoyed only by people I have consented it to be listened to. A second copy of this device will also be sent to the NSA’s headquarters in Maryland, but without the private key needed to decrypt it; a reminder that the rules of mathematics are more powerful than the rules of even the most powerful states.
We got in touch with him and was happy to answer a couple of questions for the blog:
Z: What makes you more uncomfortable about NSA actions which made you react and build this device?
D: The NSA’s mass surveillance encompasses a lot of programs which run counter to what I feel is a fundamental right to privacy. In the US Constitution there’s an expression of that in its fourth amendment.
What the NSA is doing goes against the spirit of that much like petting a cat backwards; It’s the wrong direction to go towards and a cat/society will swipe its paw at the offender.

Z: Arduino community is always interested in understanding how things are made. Where we can find source code and technical specs to build one? It would be great if we all could share more practical knowledge on these topics.
D: The mixtape device is basically just an Arduino and Adafruit wave shield. The code to play each wave file on the SD card on a loop (when unencrypted) is right off their list of examples.
I made one slight modification, which is to turn on a purple LED to indicate when it’s working. Purple is not an easy LED color to source, but it’s the global Pirate Party color and I wanted to give them subtle props for working towards a free and secure internet on the policy side of things.
I will at some point publish a way to do the encryption part of this using a Beaglebone Black and CryptoCape to make it a fully open hardware proof-of-concept, but in this case the SD card encryption was done off-device. I also plan on going through a full tutorial based on that at this year’s Open Hardware Summit in Rome.
Z: You said: “The NSA can read my stupid Facebook updates but without my consent it will never be able to listen to my kick-ass mix tape, even if it’s sitting right in front of them.” – What makes you believe that your encryption is strong enough?
D: The truth is that everyone sucks at information security, including myself, so no one can really make the claim something they’ve built is “NSA-proof.” Generally though, the less hardware and software you have, the less complexity and thus, opportunity for attack vectors or human errors there are. The playlist was kept offline, is not on the Arduino sketch, or anywhere in the hardware except encrypted in the SD card. The only place the audio existed aside from in the various sources I collected it from was on the hard drive of the PC I used to compose the mix tape, which has since been removed and stored offsite and offline. The encryption was also ran by a different machine, and one that I generally keep on my person. This goes beyond mass surveillance capabilities and into TAO/FBI “partyvan” surveillance; I can’t imagine an intelligence analyst is going to go to their very serious boss to explain that they need to expense a vehicle to go after some guy’s mix tape in a city where they won’t even be able to find a parking spot close enough to run a tempest attack from.
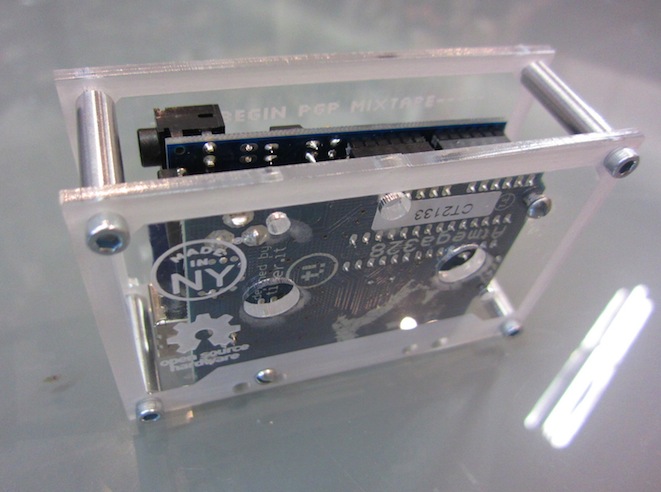
ZDo you have the pictures of the inside showing the components and the circuits?
D: They’re not too exciting since its just the Arduino + Wave Shield, but I attached a photo of the unencrypted version (clear acrylic instead of red clear acrylic), which I’ll also be bringing with me to the Open Hardware Summit.

Looking forward to meet him at Open Hadware Summit!
 For their entry into the 2019 Hackaday Prize, [Arduino Enigma] is looking to shine a little light on one of these unusual variants, the Enigma Z30. This “Baby Enigma” was intended for situations where only numerical data needed to be encoded. Looking a bit like a mechanical calculator, it dropped the German QWERTZ keyboard, and instead had ten buttons and ten lights numbered 0 through 9. If all you needed to do was send off numerical codes, the Z30 was a (relatively) small and lightweight alternative for the full Enigma machine.
For their entry into the 2019 Hackaday Prize, [Arduino Enigma] is looking to shine a little light on one of these unusual variants, the Enigma Z30. This “Baby Enigma” was intended for situations where only numerical data needed to be encoded. Looking a bit like a mechanical calculator, it dropped the German QWERTZ keyboard, and instead had ten buttons and ten lights numbered 0 through 9. If all you needed to do was send off numerical codes, the Z30 was a (relatively) small and lightweight alternative for the full Enigma machine.