
Bruce Sterling went to Thingscon conference with a keynote about Casa Jasmina and then published the following essay.
—————-
This is the third of my Casa Jasmina essays. It’s about the recent “ThingsCon” conference in Berlin, May 2015.
This remarkable event was the second “ThingsCon,” a new gathering which makes itself useful to the European hardware startup scene, especially “connected products” designers and builders from Berlin and London. “ThingsCon” took place in Berlin’s “Culture Brewery,” which is a huge, defunct beer factory, currently re-zoned for theaters, bars, restaurants and design retail.
Anybody who has seen the Garrone Foundry (which houses Toolbox Co-Working, Fab Lab Torino and Casa Jasmina), would surely recognize the “Culture Brewery.” It’s the same European story: the old industrial hulk remade for today’s culture-industry. So we found the ThingsCon venue to be pretty cozy, even though the stairs are of odd sizes, the huge, lofty rooms don’t fit together properly, the events and workshops are on different floors and mysteriously distant from one another, and there was excellent beer everywhere and tiny, crooked bathrooms stuck nowhere in particular. There’s something fun about this steampunk disorganization — if you’ve built a weird open-source Internet-of-Things device out of glued plywood and steel rods, it really fits that atmosphere.
ThingsCon is not a Maker Faire for the general public, and attending it is not cheap. ThingsCon is aimed at designers, developers, engineers, entrepreneurs and similar stakeholder-types from the technology ecosystem. The presentations were full of practical wisdom about commercial tech-product development: scaring up funding money, allocating time and resources, packaging, promotion, marketing, founder exit-strategies, angel investment, the issues common to people who might like to sit down for a serious talk with, say, Intel.
The organizers of ThingsCon are Peter Bihr, Simon Hoher, Emanuel Schwarz, Max Kruger, Sonja Heinen, Alexandra Deschamps-Sonsino, Brady Forrest, Louisa Heinrich, and Marcel Schouwenaar. As conference organizers go, they won’t win any prizes for sleek efficiency. However when it comes to the Internet of Things, these activists know plenty. At ThingsCon you can learn a lot in a hurry.
So: now that we understand what ThingsCon is about and who ThingsCon is meant to please, let’s confront some of their native ThingsCon problems, because they have lots of interesting issues.
The guy who delivered the first ThingsCon opening keynote, Warren Ellis, really understands their pains. Warren Ellis is pretty well known as a comic book writer, film scriptwriter and novelist, but he was also in the brain-trust of BERG,the legendary and now-dead London interaction-design firm. Warren Ellis grasps the many thorny difficulties of modern connected-product design.
Ellis delivered a sardonically funny rant, warning designers, engineers and manufacturers about the fierce wrath of genuine consumers. Consumers — (they’re the people who are supposed to buy Internet-of-Things products) — are a fickle and treacherous group. Consumers are never grateful for the hard work of designers and technicians. On the contrary, consumers are suspicious, endlessly demanding of customer support, and they resent most things they buy. The Internet-of-Things is even worse than traditional consumer capitalism, because interactive products don’t just sit there, they are invasive and intimate. People treasure their homes as a safe space in a harsh, competitive world, and they feel emotionally wounded when anything in their house betrays them.
Warren Ellis is an intelligent and erudite man, and he was telling the crowd the truth, but they were all laughing nervously because they can’t really believe what he says. It’s all true, but it’s important to understand this and still have some courage about it. If you invent and manufacture something, and it’s a commercial success and ten million people buy the product, of course your life is going to change. You won’t be a “Maker” alone in a garage any more, you’ll be an Internet multimillionaire with customer-support issues. Warren Ellis is right to urge people to think these things through: you shouldn’t dabble in technology and business unless you’re ready to face the consequences of getting what you want.
Barriers to entry in manufacturing are collapsing, so the old lines between a do-it-yourself Maker and a commercial industrialist are blurring. But this doesn’t solve old problems, it just creates interesting new ones. This was the lesson conveyed by Tina Aspiala. Before ThingsCon 2015, I had never heard of Tina Aspiala. Thanks to ThingsCon, I will pay attention to Tina Aspiala from now on.
Tina, who achieved some success with a product of hers, has become a Kickstarter patroness. Tina Aspiala spends a lot of time on Kickstarter and likes to give people some crowdfunding money just to see what happens. She told the crowd that results were mixed. Kickstarter is a funding platform, but some people on Kickstarter are crooks, they’re Kickstarter embezzlers. Other people want to be honest, but they flee in terror when they realize what the real world expects from real design and manufacturing. Others just have bad luck with their Kickstarter: they really wanted to do the work, but they broke a leg, or Dad died, or there was a divorce… that mishap wouldn’t stop FIAT or General Electric, but it does stop the Kickstarter team because they are few in number, while FIAT and General Electric have thousands of personnel.
Many Kickstarter projects get built, despite the host of problems in shipping, supply chains, material costs and manufacturing — but that doesn’t end the story. The product might be workable, but just not much good. The product might do what is promised, but the thing that the product does is only interesting once or twice, not useful in daily life. It’s a “gonzo product” (in the term created by Alexandra Deschamps-Sonsino), because it physically works and it does something, but the thing it does is eccentric and weird, so it has no commercial potential or mass appeal.
Why do we have “gonzo products” nowadays? It’s because (as Tina Aspiala pointed out), cheap electronic components make new combinations easy. Projectors, motors, sensors, cameras, processors and various wireless connectivity chips are all drastically cheaper, so product development becomes like a card game, when any gambler can connect X with Y and add some Z, then hope for a jackpot payoff.
In the case of the Internet of Things, there are many possible inputs — dozens of sensors of all kinds — but very limited outputs, because most IoT gizmos can only do very limited things to get any human attention: they blink, or beep, or vibrate. Blinking, beeping, vibrating things that demand human attention can get pretty annoying. Clearly this is a major IoT problem. Tina Aspiala recommends trying to think this situation through with some design perspective, instead of just hacking more components and attaching them to breadboards with soldering irons. That’s a point of view that makes some sense, though, let’s face it, people are gonna want to do it the easy way.
ThingsCon abounded in talks and workshops, more than I can describe here, but the most interesting thing on offer at Thingscon 2015 was the “IOT Design Manifesto”. That’s why I’m placing the manifesto here in this post.
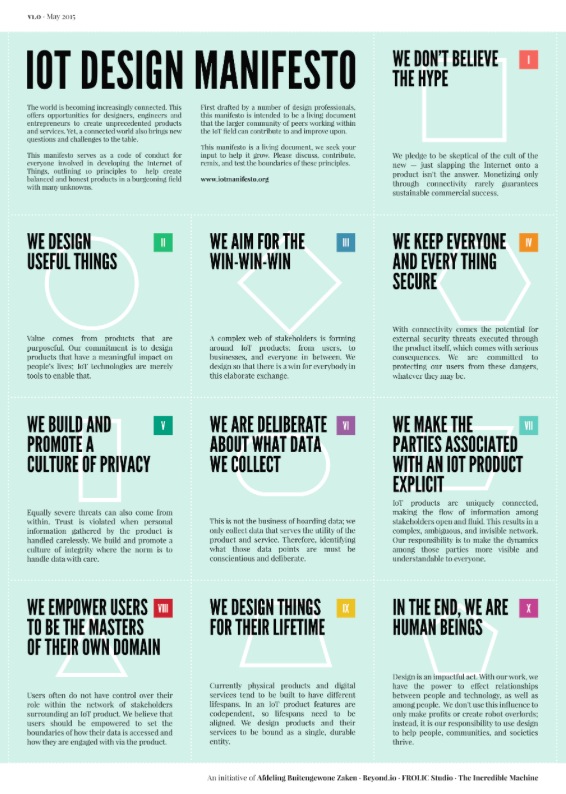
A manifesto is a sign of creative health. It’s not that I agree with the “IoT Design Manifesto” — on the contrary, if everybody agrees with a manifesto, then the manifesto is vapid and useless and hasn’t really said anything. Even a manifesto that’s completely wrong can be useful, because it motivates people to rebel and try something else. This manifesto is pretty good, in my opinion, because it’s kindly in tone and well-mannered, it confronts quite a few of the IoT’s real problems.
Even the first declarations, one and two, “We don’t believe the hype, we design useful things,” singles out the ThingsCon crowd as people who are skeptical and yet also trying to get something done. It’s a good attitude for a young industry. The other declarations are about about participation, security, privacy, data collection, association, personal agency, sustainability and humanity. These are some big, hairy issues which aren’t going to get solved in anybody’s lifetime. However, if you spend your life with the Internet of Things you’re going to be dealing with situations of that kind all the time. So, might as well get used to that prospect now.
The authors of this IoT Manifesto are Andrew Spitz, Ruben van der Vleuten, Marcel Schouwenaar, Harm van Beek, Kevin Verelst, Anner Tiete, Jan Belon, Marcel van Heist and Holly Robbins. Before I went to ThingsCon I’d never heard of any of those people, but they were right to do what they did, and I’ll be watching them with a lot more interest from now on. People tend to grow by the size of their chosen problems. These people have some pretty big problems.
I closed the ThingsCon event by asking the people there to help us with our house.
It’s a bit scary to open the faucet in this way: we don’t know if we’ll get a huge flood, or just a groan in the pipe and some dripping. If we get a lot of interest, Casa Jasmina will be crowded and noisy; if interest is more modest, we’ll try to concentrate on a few core issues. In our Internet-of-Things house, we’ll have to acquire some things, accept some things, build some things and maybe commission some things, too. The project has started deliberately, we have paced ourselves, but as the months pass, Casa Jasmina will slowly become a unique and interesting place, a true place of difference.
I wondered, in starting this project, who would ever really want to stay in such a place, and, having been to ThingsCon, I now have a much better idea about that. ThingsCon had about 300 people attending it — the “new hardware movement” are not a mass movement of millions — but those three hundred people are real people. They are bright and committed, and they really exist. If we understand them as our natural guests and we try to please them, I think we’ll do well.
Bruce Sterling
 A team of researchers were able to unlock and start the ignition of Volkswagen cars with just $40 of electronic components.
A team of researchers were able to unlock and start the ignition of Volkswagen cars with just $40 of electronic components.
![The encoding scheme used by [Ido].](https://hackadaycom.files.wordpress.com/2015/08/encoding2.jpg?w=800&h=240)









